Vaultwarden with Docker on a Synology NAS
Install password manager Vaultwarden on a Synology NAS under Docker.

Table of Contents
CAUTION
Please be aware that the original version of this blog post was written in German. This English translation has been provided for your convenience. While all efforts have been made to maintain accuracy, there may be some translation errors. I apologize for any confusion or misunderstandings that may arise from the translated text. Corrections are welcome via comments or email.
Strengthening Digital Security with Vaultwarden on a Synology NAS
In today’s digital age, secure password management is non-negotiable. With the myriad of accounts and applications each of us uses, safeguarding personal information begins with robust passwords. Celebrating World Password Day, let’s delve into installing Vaultwarden, an open-source password manager, on a Synology NAS using Docker.
Discovering Vaultwarden
Vaultwarden, a Bitwarden derivative, is a free and open-source tool that simplifies password management. It enables users to generate and securely store unique passwords for every login, presenting an effective alternative to proprietary password managers. Vaultwarden shines with its straightforward interface yet comprehensive feature set.
The Logic Behind Docker Deployment on Synology NAS
Leveraging Docker to run Vaultwarden on a Synology NAS encapsulates the application in a container, ensuring isolation from other system components. This method simplifies installations, migrations, and updates significantly.
Prerequisites for Vaultwarden Installation
For my setup, I use a DS220+(Amazon affiliate link)Synology NAS equipped with 10 GB RAM(Amazon affiliate link), although Vaultwarden’s modest resource demands are as follows:
| System requirements | Minimum |
|---|---|
| CPU | 0.2 cores |
| RAM | 128 MB |
| Storage | 200 MB |
These guidelines also apply to other Docker-compatible devices.
A reverse proxy manager is essential within the network, whether hosted on another device or directly on the Synology NAS. A domain is also beneficial.
Setting the Stage for Installation
Before diving into Vaultwarden’s setup, ensure Docker is installed on the NAS. I’ve detailed the DiskStation setup process here. While Portainer is optional, it’s a useful tool for managing containers. I’ll focus on using Portainer in this guide.
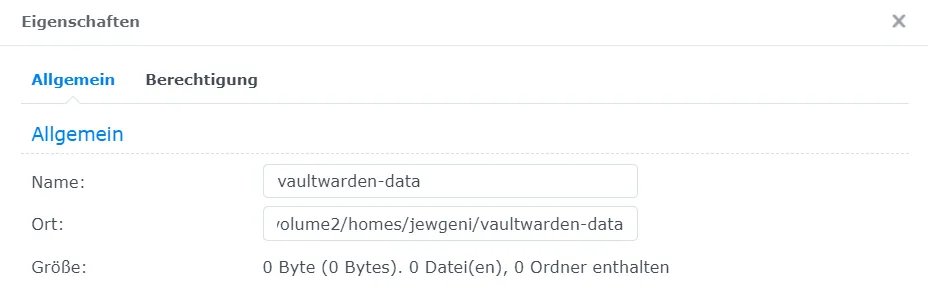
Firstly, create a dedicated folder for Vaultwarden’s persistent data. Note down the folder path after naming it vaultwarden-data.
Deploying Vaultwarden
Commence the installation by configuring a new stack in Portainer using Docker-Compose:
version: "3"
networks:
internal:
external: false
services:
vaultwarden:
container_name: vaultwarden
image: vaultwarden/server
restart: unless-stopped
volumes:
- /path-to-folder:/data # Modify to the actual folder path on your NAS e.g., /volume1/docker/vaultwarden-data:/data
ports:
- 1234:80 # Change the left side port as needed
- 3012:3012 # Change the left side port as needed
environment:
- WEBSOCKET_ENABLED=true # Enables real-time sync
- ADMIN_TOKEN=secure password # Admin login token
networks:
- internal
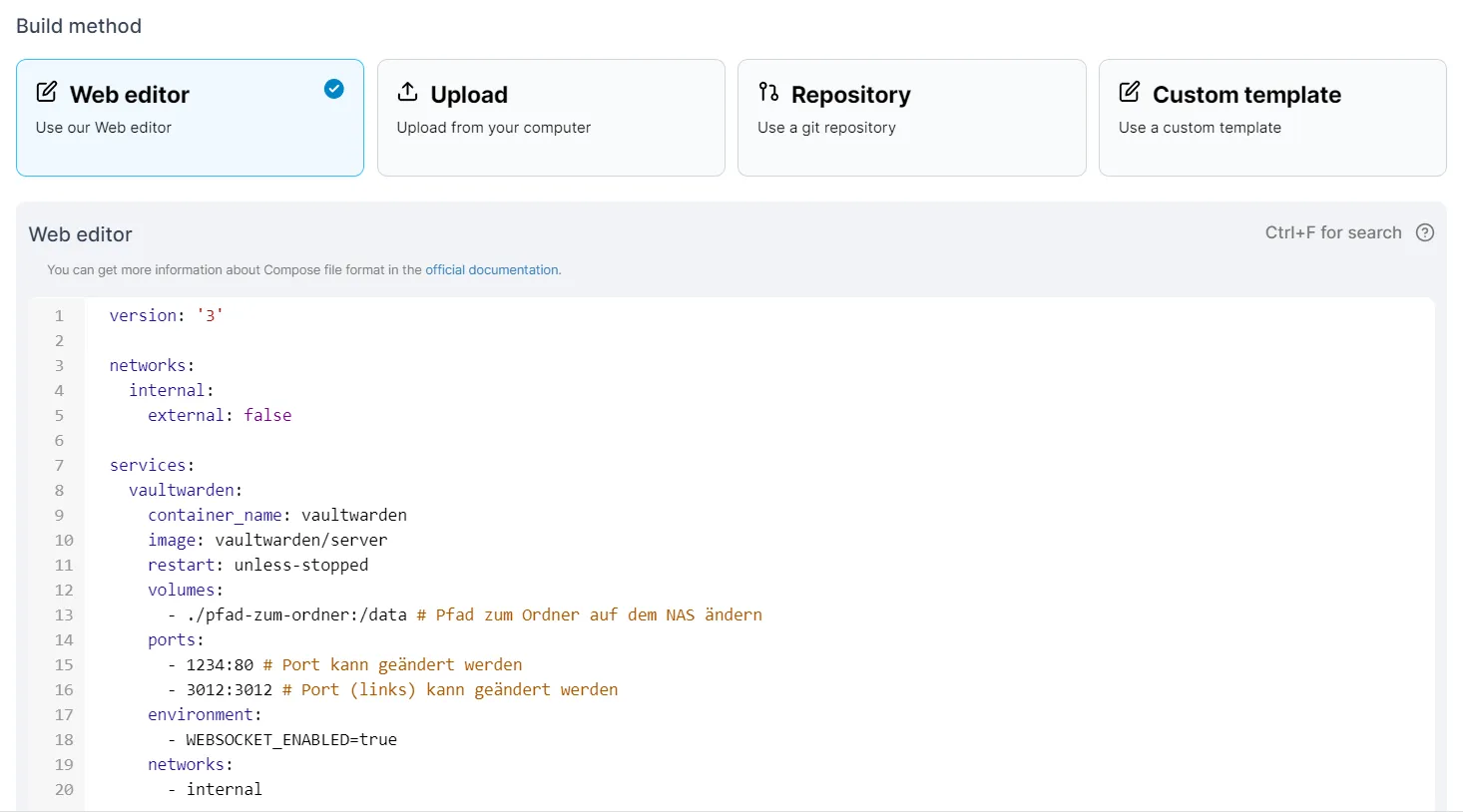
If utilizing a proxy manager on the DiskStation, integrate the proxy manager’s network and omit the port configurations.
After stack creation, monitor the container’s log to confirm the server is operational.
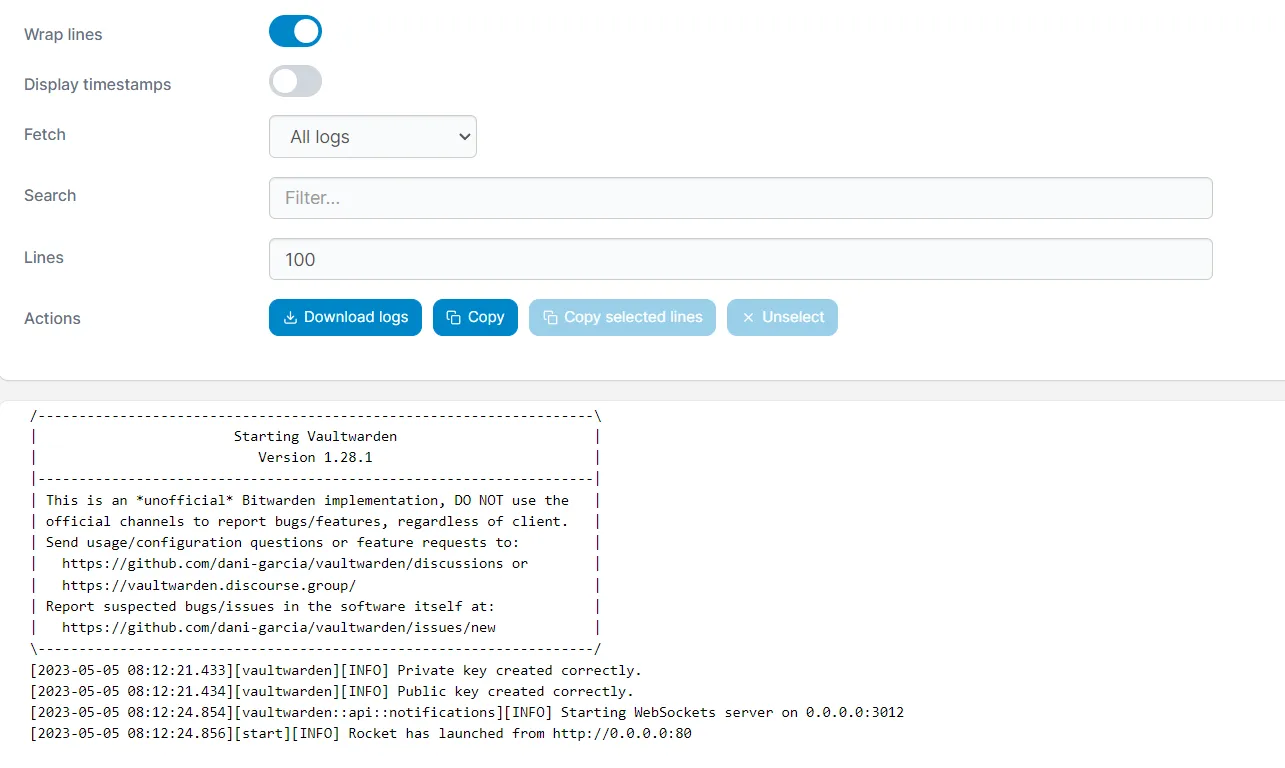
Configuring Vaultwarden
Establishing a Proxy
Setting up a proxy host varies depending on the reverse proxy used. Here’s how it could look with Caddy:
# Input your domain here
vaultwarden.domain.de {
encode gzip
# Reference ports from docker-compose.yml and NAS IP
reverse_proxy /notifications/hub/negotiate 192.123.123.40:1234
# Websocket port from docker-compose.yml
reverse_proxy /notifications/hub 192.123.123.40:3012
# Redirect to the first port again
reverse_proxy 192.123.123.40:1234
}
For Nginx Proxy Manager:
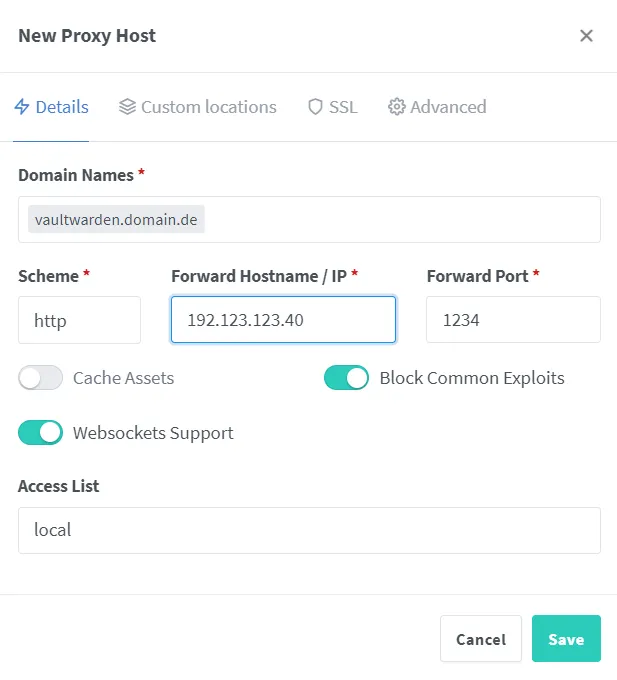
Secure Vaultwarden with a Let’s Encrypt SSL certificate.
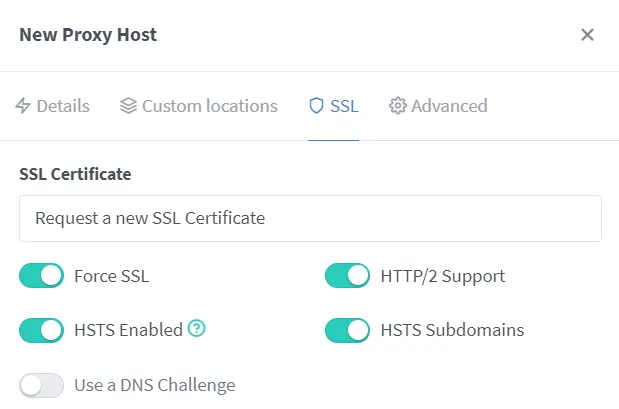
Configure advanced settings accordingly:
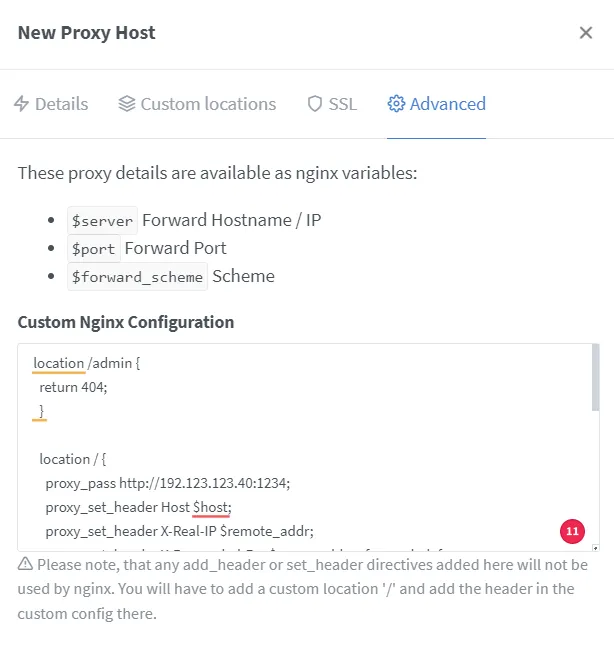
# location /admin {
# return 404;
# }
location / {
proxy_pass http://192.123.123.40:1234;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /notifications/hub {
proxy_pass http://192.123.123.40:3012;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
}
location /notifications/hub/negotiate {
proxy_pass http://192.123.123.40:1234;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
Adjust ports and IP addresses as required.
Initial Setup and User Management
Navigate to the URL to register a new user account.
Access admin settings using the admin token from docker-compose.yml by appending /admin to the URL. Configure the domain under “General Settings” and manage user registration options here.
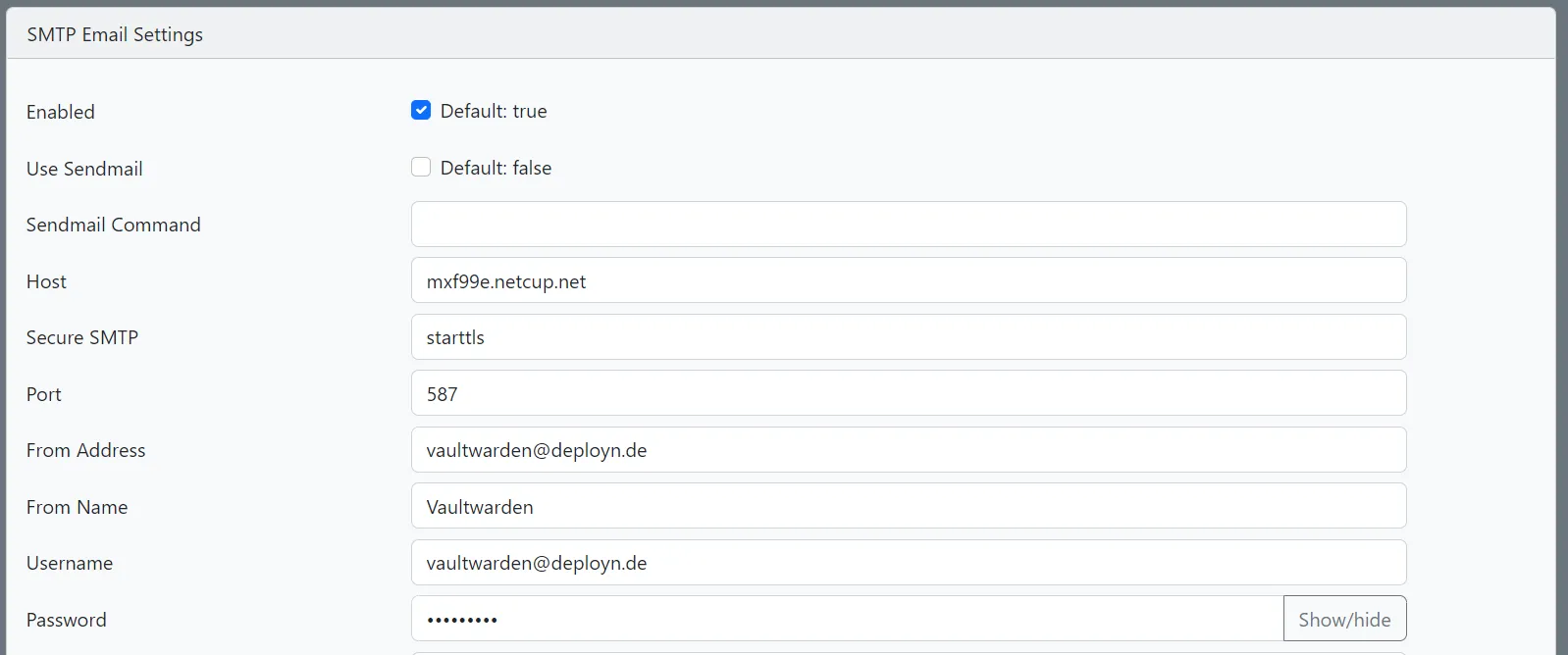
Set up “SMTP Email Settings” to enable Vaultwarden to send emails.
Invite new users under the “Users” section.
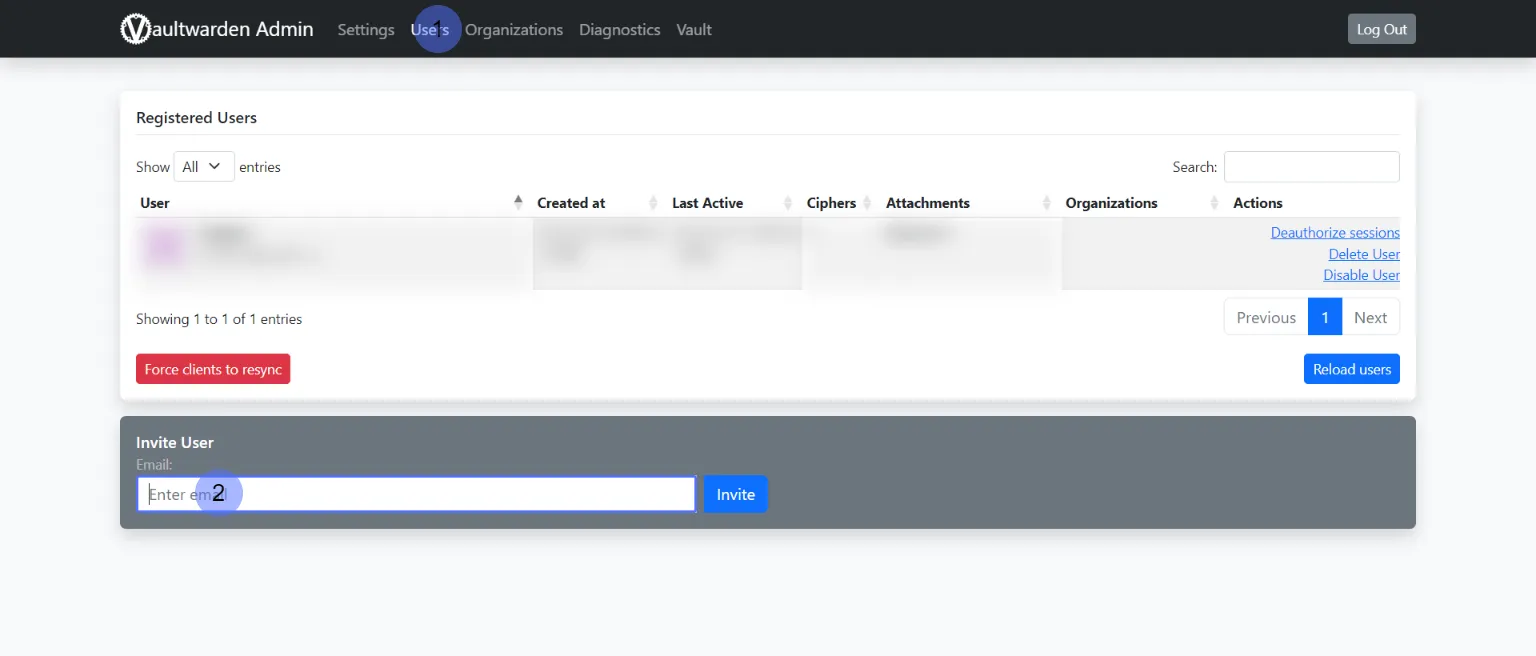
Optionally, secure the admin area by uncommenting the relevant lines in your proxy manager’s settings:
location /admin {
return 404;
}
[...]
Keeping Vaultwarden Up-to-Date
Updates are straightforward with Portainer. All you have to do is recreate the stack. To do this, go to the stack editor in Portainer and click “Update the stack”. Select that the image should be rebuilt.
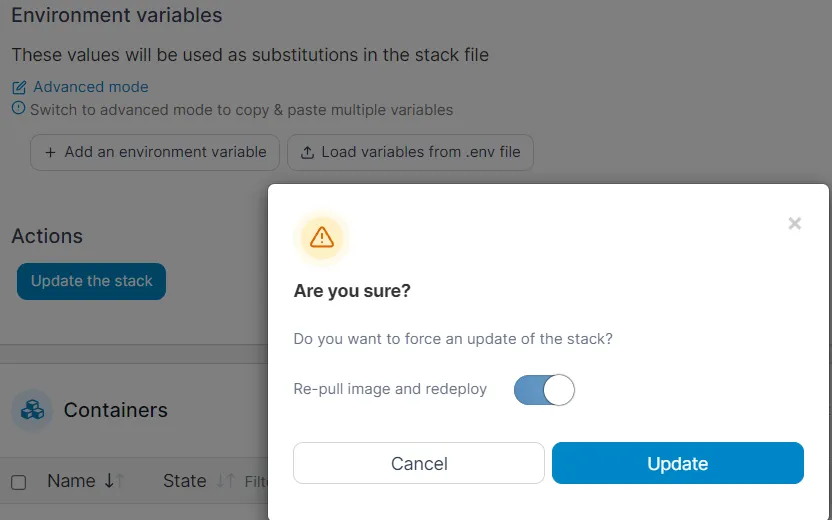
If there is a new release, this should be downloaded and started using the procedure.
Summing Up
Vaultwarden stands out as a viable Bitwarden alternative, with simple installation and convenient administration for multiple users. While reverse proxy configuration adds complexity, it’s manageable with clear instructions. May this guide serve you well in bolstering your digital security.